Lately, we have had a lot of interest regarding VPN’s, and why they are sometimes necessary when operating your business in the Cloud. The internet is full of technical documents that can make even a seasoned Technical Rep feel uncomfortable. The idea of this post is to keep our customers informed without being overly technical so that you and others can benefit from what Hostek and the Cloud has to offer.
Here are some of the questions we get asked most often:
“What is a VPN and why would I need one?”
“What are the differences between Client VPN’s (client to site) and Site VPN’s (site to site)?”
“Which VPN solution is right for my business, or will I need both?”
“Do I need to set this up or do you?”
So let’s take the time to understand what a VPN is.
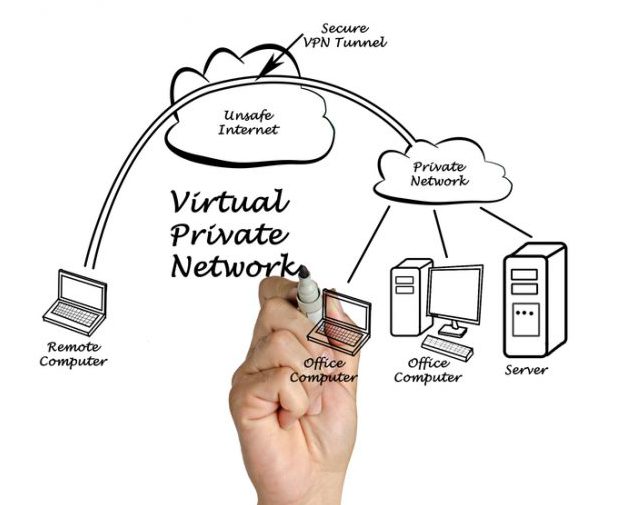
The best place to start is with a non-technical definition. The acronym VPN stands for “Virtual Private Network”. It’s a feature or application usually built right into most Gateways or Edge devices that allows you to leverage the internet to connect remote networks. It’s usually the device in your office which connects directly to your ISP modem and gives you access to the internet. At Hostek it’s software installed into a virtual machine, but we can discuss that in more detail some other time.
A VPN’s greatest benefit is the ability to span the internet in order to create your own private network to your cloud services. The VPN creates a single networked entity by securely connecting your local network with a remote network. Any communication sent from one side is encrypted until it reaches the other side where it is decrypted. So rather than try to establish individual security protocols for each application or function, you can do so using a single VPN solution that encrypts all communication (sent over the VPN tunnel).
So now let’s discuss the two main types of VPN’s.
The first is a “Site to Site” or Site VPN’s.
So a Site to Site VPN is setup on 2 separate gateways, one at each endpoint. These two gateways can be as close as the next building, or as far apart as continents in separate hemispheres. As long as both sides have access to the internet and are configured appropriately.
A Site to Site VPN requires a small amount of configuration to be agreed upon so that it matches on both endpoints. Both sides would need the other’s public IP so that each device can find the other. Both sides would need the other’s LAN configuration so that both gateways will know what traffic to send to the other. Both sides would agree on the method of encryption (3DES, AES, or AES256), various timeout values, and a few other miscellaneous settings.
One of the most important factors of the Site VPN is its ability to stay connected indefinitely after the initial setup as long as there are no connection issues or mis-configurations. So you can expect to have constant access to the remote LAN from either side.
Now, we move on to “Client to Site” or Client VPN’s.
Client VPN’s are different in that they only require one gateway of the network you wish to connect to. Client VPN’s can have one to many clients that might need to connect. In this scenario a client VPN software package is installed on the remote user’s PC, and is used to connect to the configured gateway.
This virtually adds their computer to the “local” network as if they were on site themselves. Much like the site to site VPN, all communications are encrypted. This is great when you have mobile clients that need on demand access to the hosted resources that is accessible on any type of internet, located anywhere in the world.
In this scenario I would configure the router for VPN access and setup individual user accounts. Then I would create individual client packages so that I can send to the clients to be installed on their computers. These clients would install the VPN software and only connect as needed, usually with built-in certificates and/or login credentials as the authentication method.
Site and Client VPN Conclusion
Both are acceptable means of encrypted communication. These VPN technologies can be used individually or together depending on the requirements necessary.
So if you’re thinking about putting your business in the cloud, or even if you already have; at some point you need to start planning for all possible scenarios.
Possible VPN Scenario
How will you upload or migrate highly sensitive data from your local network to your VPS securely?
What encryption method will your local office use to interface securely with your Hosted VPS applications?
How can we make a truly private database not publicly accessible but still have access to manage and update it as needed?
How can developers gain access and make changes securely but still give me the authority to control it?
These are all questions that can be answered correctly with the implementation of the right Edge Device and VPN solution.
Summary
Hostek has helped many companies, universities, hospitals, etc. that deal with sensitive data, requiring strict compliance like HIPAA with their site to site VPN needs and/or their client to site VPN hosting needs.
I encourage you to schedule a consultation so we can go over your hosting and/or VPN needs. Not everyone needs a VPN. But if you do, we are here to help! Hostek has the most awesome 24/7 U.S. Support Team and can handle most any hosting need.
Click here to schedule a free server consultationCategories: Developers, Hosting


